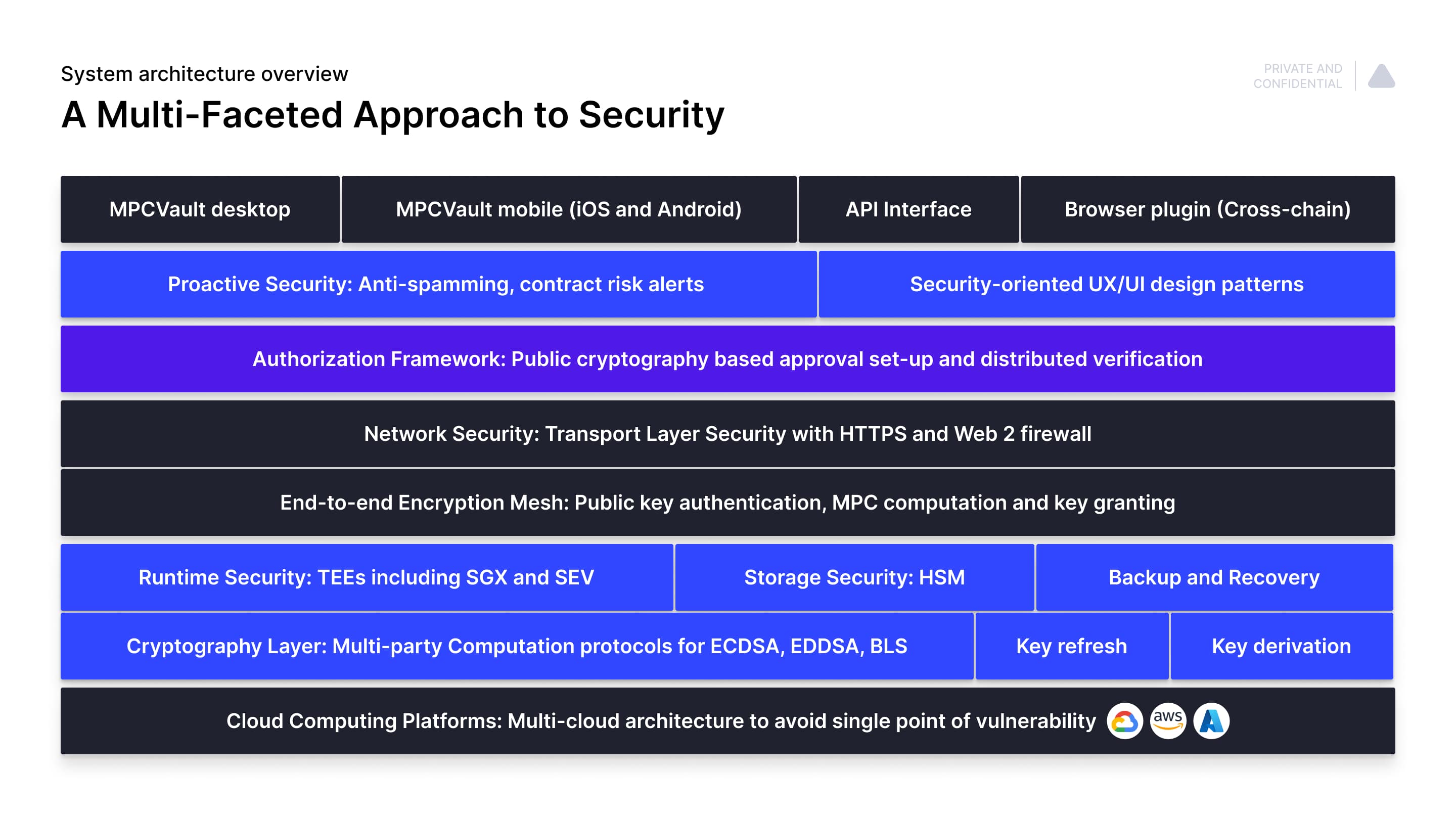
Technical Overview
Architecture
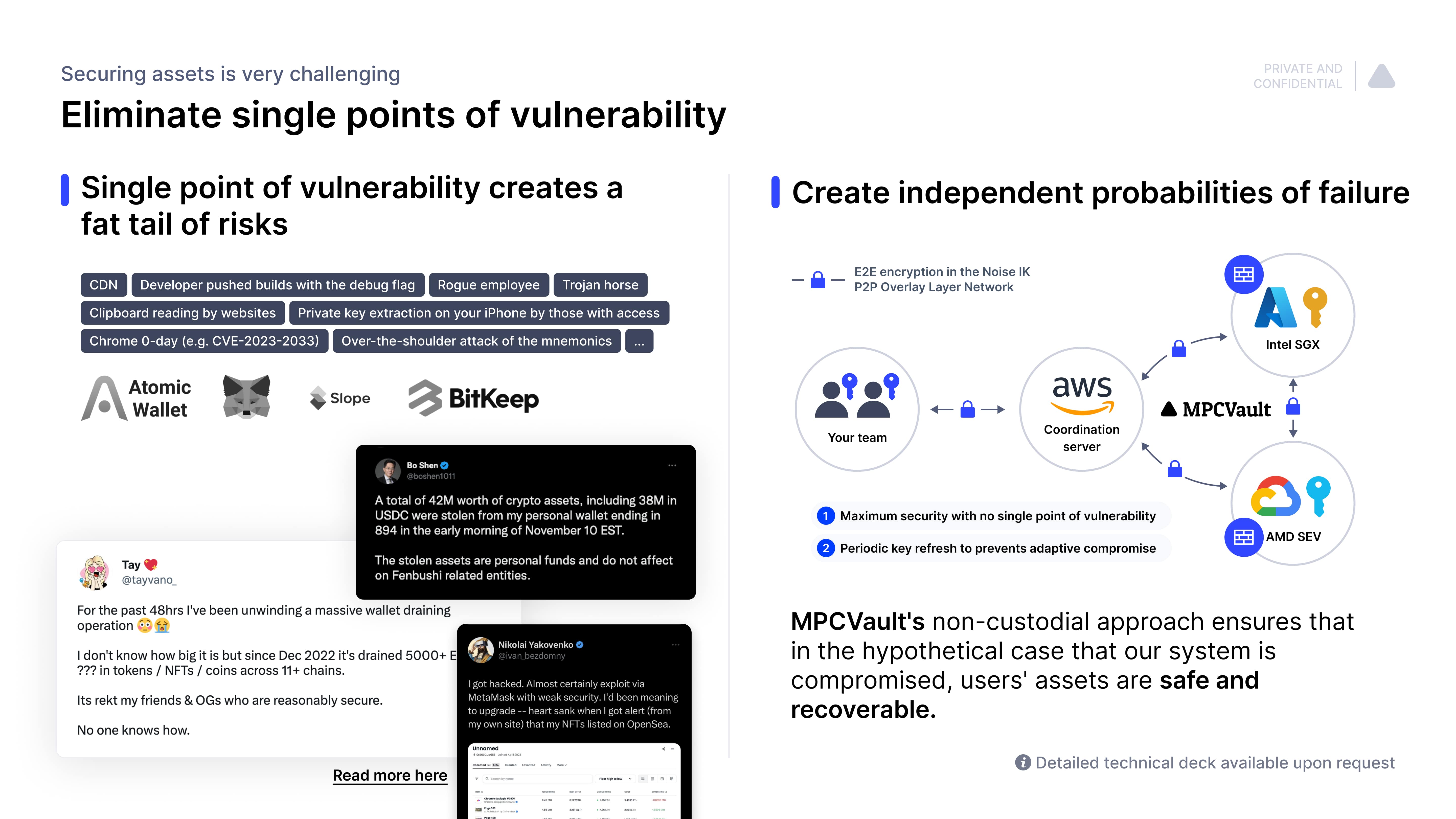
There are three rotating key shares: you hold one, and MPCVault holds the other two in different cloud environments with multiple encrypted backups worldwide. All three key shares are required for signing.
You can request the two key shares from MPCVault or request a Trust to hold an encrypted backup for recovery, independent of MPCVault.
Counterparty risks are significant in the crypto industry, as we have seen in the recent bankruptcies of 3AC, Celsius and BlockFi. There are no counterparty risks with MPCVault since we do not have all your key shares. Compared to CeFi custody providers, which may take unmeasured risks with your assets, you always know where your assets are and the risk profile of your asset holdings.
Key Derivation
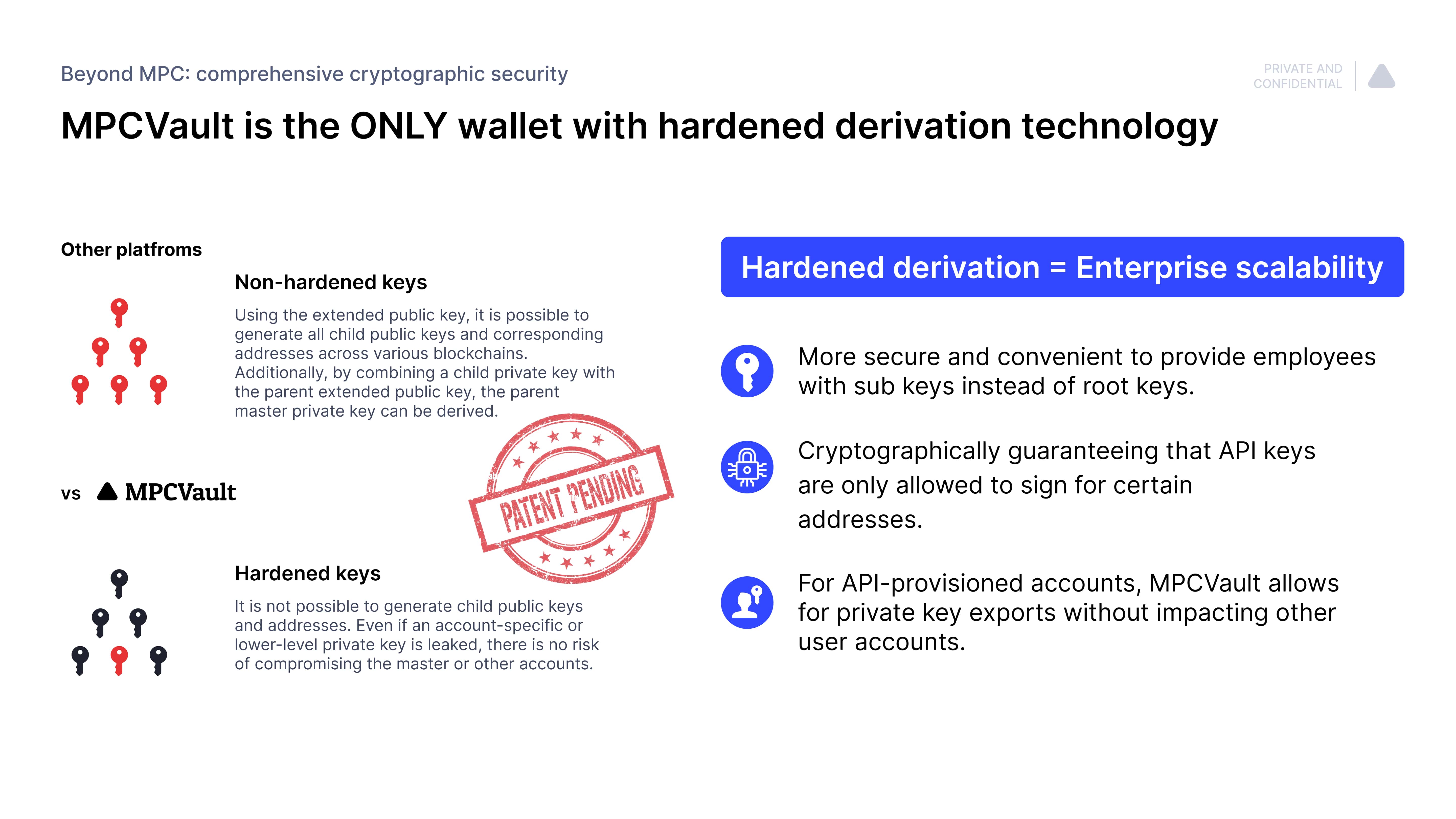
MPCVault utilizes MPC-based hardened derivation and holds a patent on achieving hardened derivation in the multiparty computation (MPC) setup.
Why is this important
In the non-MPC world, all wallets have switched to hardened derivation. However, in the MPC world, MPCVault is the only provider that has implemented hardened derivation.
Without hardened keys, even former members of your team can track your newly added assets, leaving your asset holdings vulnerable.
In the event that your child key is compromised, such as through a poorly designed signature protocol on a new blockchain, your master keys and assets on other blockchains are also at risk.
For each new asset address you create, a new derived key will be generated. This ensures isolation between various blockchains and prevents attacks like cross-chain signature reuse. Additionally, this feature allows you to generate as many addresses as necessary, providing flexibility.
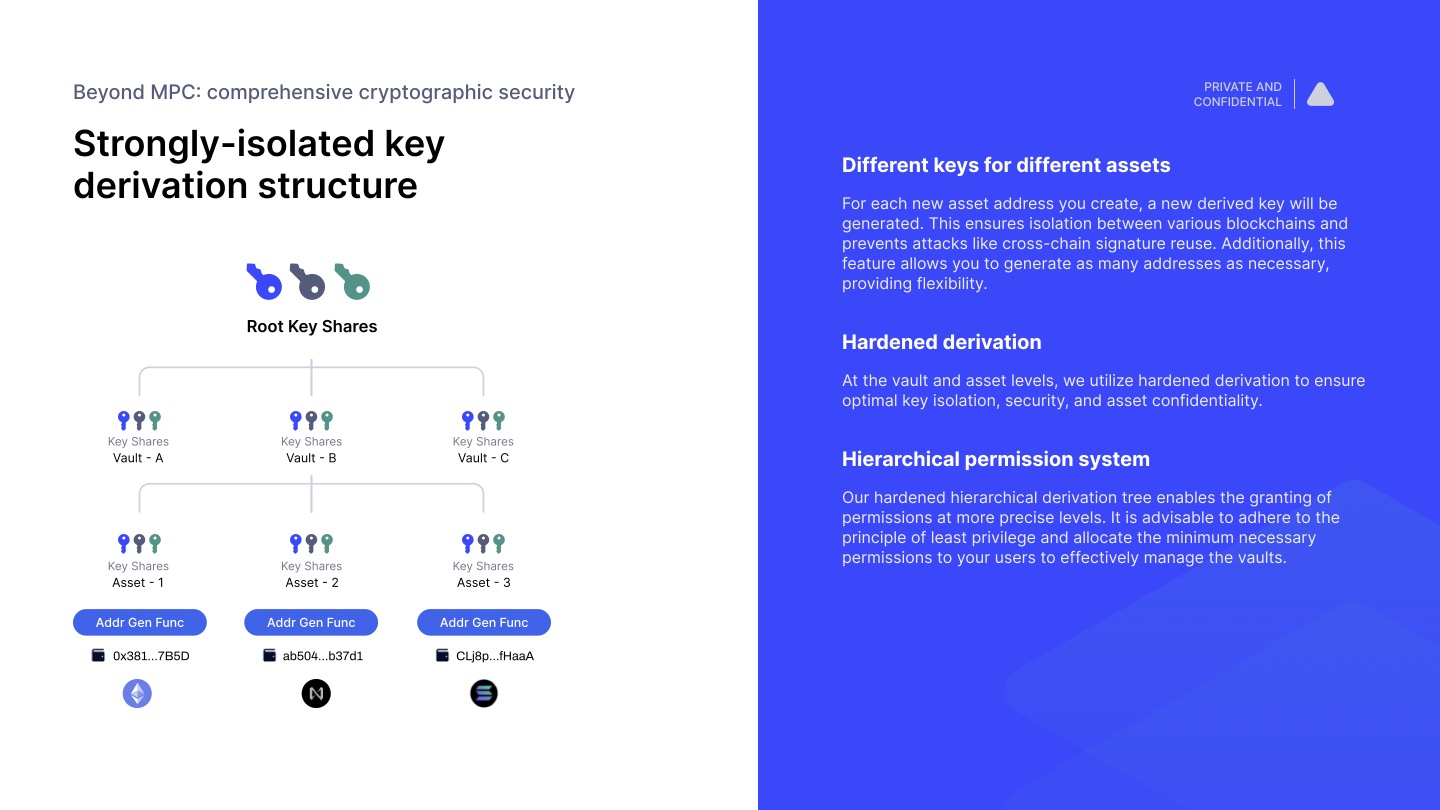
Our hardened hierarchical derivation tree enables the granting of permissions at more precise levels. It is advisable to adhere to the principle of least privilege and allocate the minimum necessary permissions to your users to effectively manage the vaults.
Key Refresh
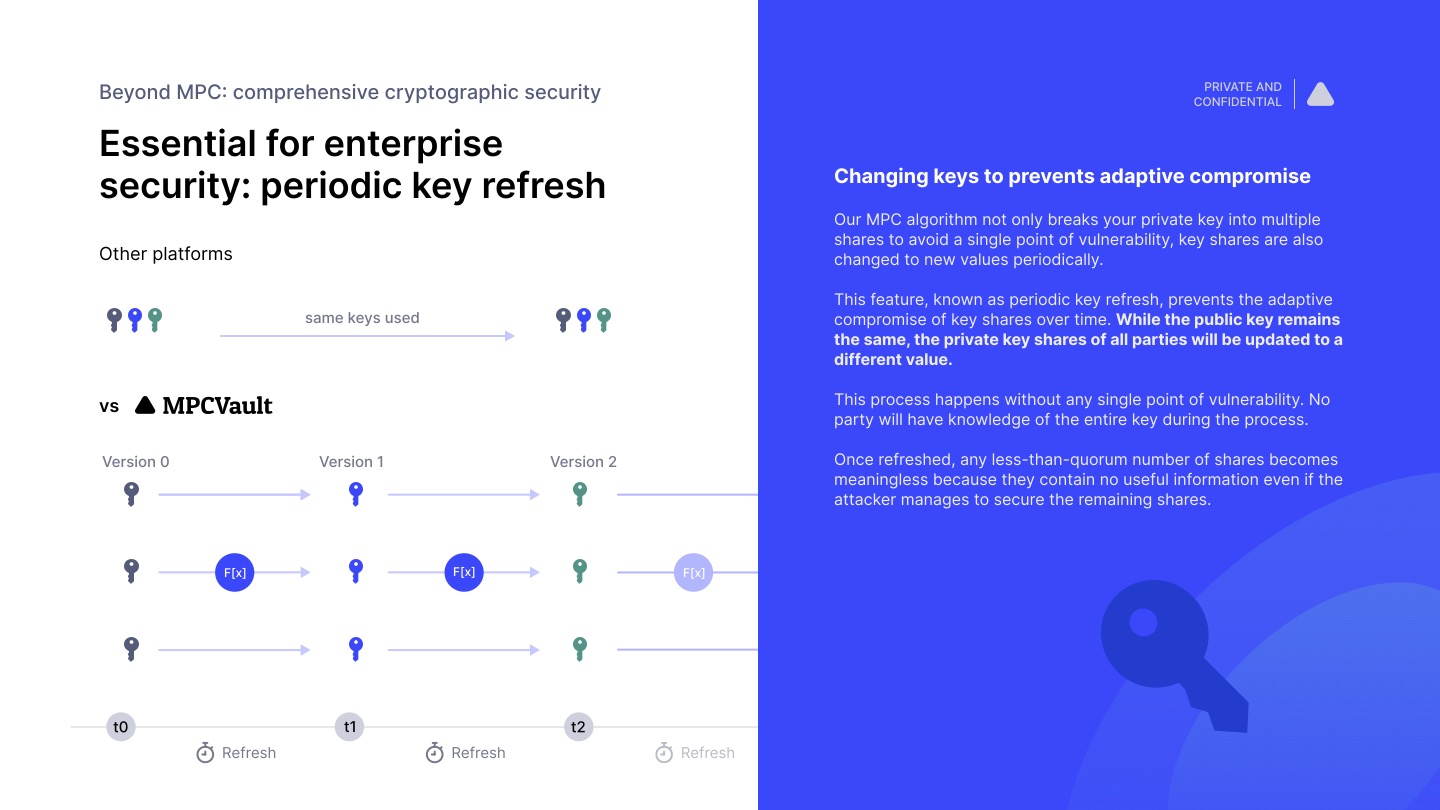
Our MPC algorithm not only breaks your private key into multiple shares to avoid a single point of vulnerability, key shares are also changed to new values periodically.
This feature, known as periodic key refresh, prevents the adaptive compromise of key shares over time. While the public key remains the same, the private key shares of all parties will be updated to a different value.
This process happens without any single point of vulnerability. No party will have knowledge of the entire key during the process.
Once refreshed, any less-than-quorum number of shares becomes meaningless because they contain no useful information even if the attacker manages to secure the remaining shares.
End to end encryption
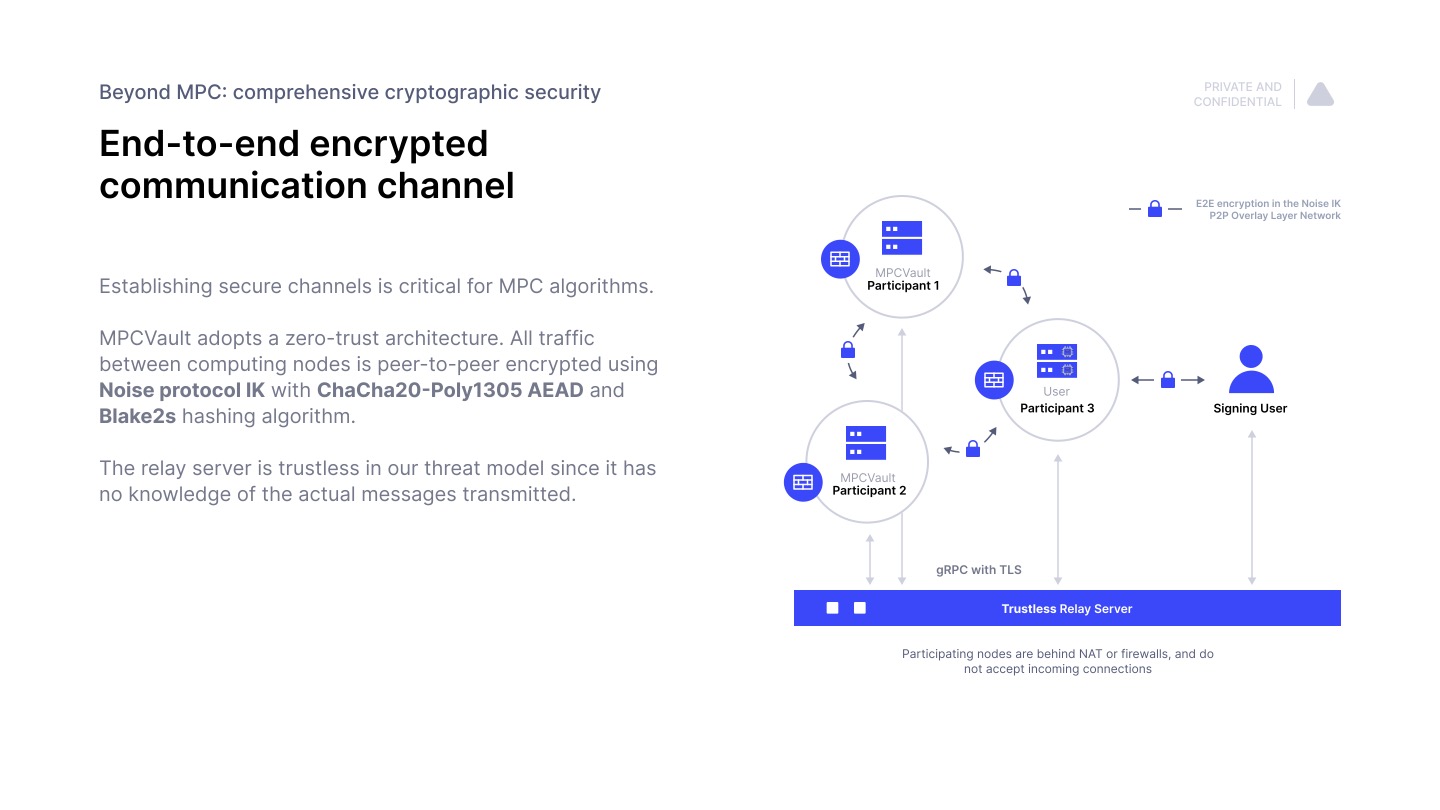
Establishing secure channels is critical for MPC algorithms.
MPCVault adopts a zero-trust architecture. All traffic between computing nodes is peer-to-peer encrypted using Noise protocol IK with ChaCha20-Poly1305 AEAD and Blake2s hashing algorithm.
The relay server is trustless in our threat model since it has no knowledge of the actual messages transmitted.
Personal Key Certificate
Each user of MPCVault will have a cryptographic identity defined by an Ed25519 key pair which is called the personal key certificate. The private key is only known by the user.
In addition to traditional platform authentication, we perform cryptographic attestation using the user's public key.
Cryptographic identities power our zero-trust end-to-end encryption architecture, enabling trustless secure secret sharing such as passing key shares from one user to another.
